Major vulnerability discovered on Linux Azure App Service (web app) platform
Another identity is provided to users, which is leading to name spoofing and leaking sensitive data.


Linux based App Service is caching cookies when CORS is enabled from Azure Portal!
-
This article demonstrates an important security flaw on Azure application services (also called Web App or Azure-websites) that
is currently live since at least the 24th of November 2019 on Linuxfixed since the 6th of January 2020. -
whenever a hosted web server is called by clients without any local cookie, the server gets the latest set cookie value in the request header as if it was a global variable.
-
As a result, this bug is leading to identity spoofing and sensitive data leaking.
-
If the web app is using cookies for managing session, permissioned data become public after a user with enough privileges logged in.
Technical details
- When the CORS settings are used to limit CSRF on the LINUX based app service and when a server responds with a set-cookie without the secure flag, like this:
'Set-Cookie': `randomCookie=test; Path=/; HttpOnly; SameSite=Lax`,-
Azure PaaS is caching the cookie value and provides the value on every future server calls.
-
As a result, whenever the server is called by clients without any local cookie, the server gets the latest set cookie value in the request header as if it was a global variable.
-
This does not occur when the secure flag is present when setting the cookie or if CORS settings are not used. This security flaw is a major concern as cookies are used for session management (session cookie, cookie storing access token, jwt, ...).
-
The nodejs App is very simple: https://github.com/jcbaey/azurewebsites-cookie/blob/master/index.js and does not contain any NPM dependencies, pure NodeJS.
-
Node 10 LTS is used with the default Oryx deployment. App service is used here as Paas.
-
Kestrel web server seems to be used (seen in the response header).
-
This issue cannot be reproduced on local nor in a dedicated VM. Only in Azure web-app.
-
as soon as I discovered the security hole, I created a severity A case on Monday 2nd of December 2019 to the support.
Microsoft statements after my report:
Products Impacted: Azure Web App (Linux)
The support professional concluded that it is a known issue, and a fix will be provided during 2020. The Microsoft Engineer has requested the product group to investigate to check if there is a fix that can be deployed earlier for [...]'s environment.
- I have also submitted the case to the Microsoft Security Response Center (MSRC) on the 2nd of December 2019.
The response comes the day after, this vulnerability was not taken seriously by MSRC:
Thank you for contacting the Microsoft Security Response Center (MSRC). We appreciate the time taken to submit this assessment.
Upon investigation, we have determined that this submission does not meet the bar for security servicing. This report does not appear to identify a weakness in a Microsoft product or service that would enable an attacker to compromise the integrity, availability, or confidentiality of a Microsoft offering.
As such, this email thread has been closed and will no longer be monitored.
The day I wrote this post, Azure app service portal was not displaying any warnings or any security notice on the CORS settings page.
- Because of my insistence, Microsoft has created a public issue on MS Github: https://github.com/Azure/app-service-announcements-discussions/issues/128
- Since the 3rd of December 2019, a fix is available on support request by the engineering team (by providing a specific environment variable in the web app settings). No ETA for global deployment.
At this time, the bug is still present in all Azure regions even if a fix is available on request.
Steps to reproduce (working on the 4th of December 2019)
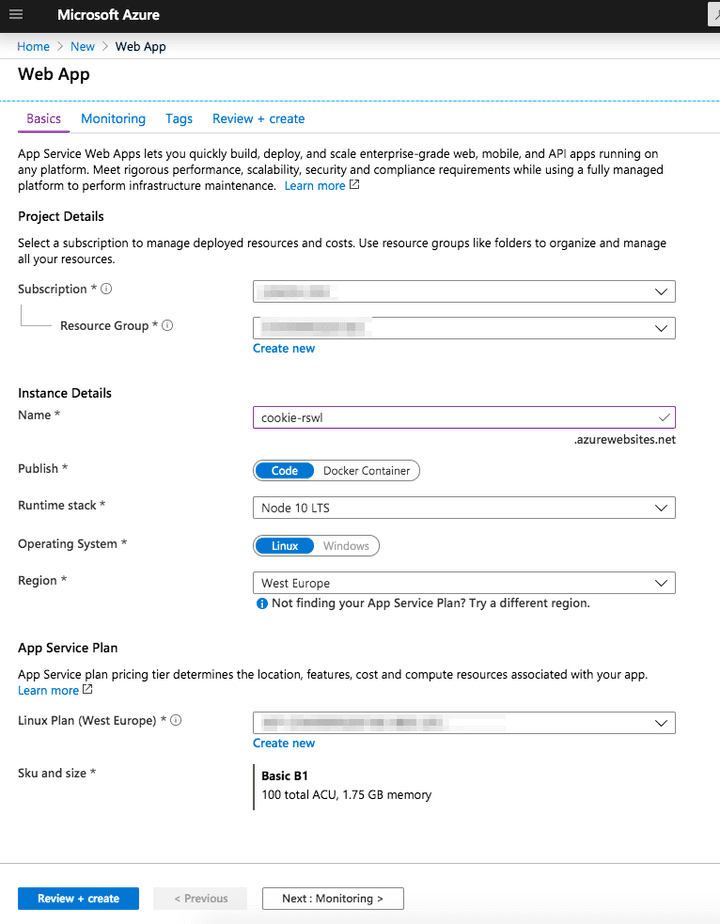
- Create a new web app using NodeJS 10 LTS + Linux
-
Once created, use the deployment center to deploy the source code available in this public github: https://github.com/jcbaey/azurewebsites-cookie
-
Open the created website
https://<your app>.azurewebsites.netfor instance https://cookie-rswl.azurewebsites.net/ -
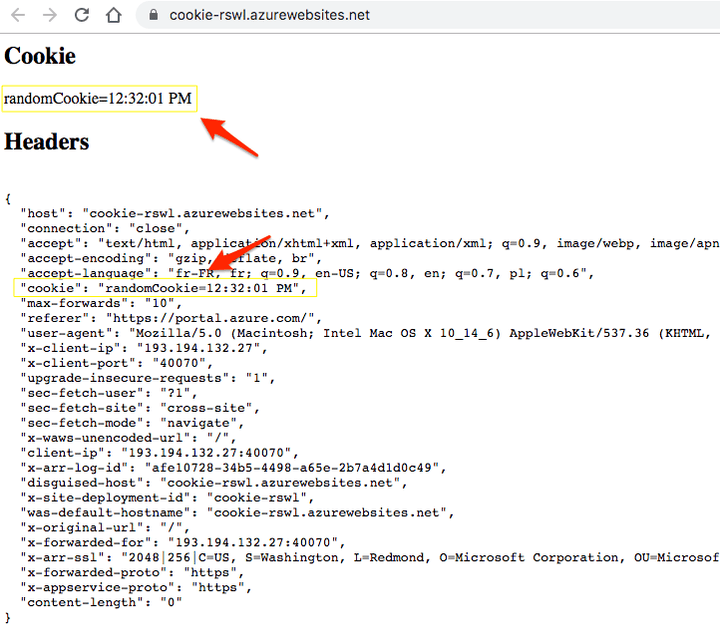
The website dumps the content of req.headers.cookie and req.headers
-
The cookie header should be empty at this step.
-
Open the page
https://<your app>.azurewebsites.net/set, for instance https://cookie-rswl.azurewebsites.net/set to set the cookie to the current time. -
Delete all local cookies in your browser or open the website in a private navigation mode:
https://<your app>.azurewebsites.net, for instance https://cookie-rswl.azurewebsites.net/ -
The cookie header should be empty at this step but THIS IS NOT THE CASE.
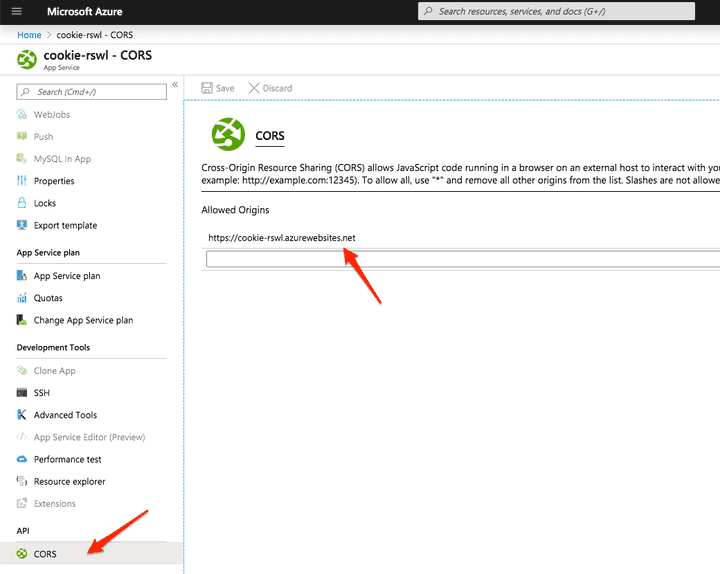
- This issue occurs when the CORS settings are used. If you have at least one entry in this page (which is the case by default, you get '*'), the issue happens:
👉 Don't forget to follow me on Twitter to be notified when new posts are available!